We have all heard the saying, “Life is a journey, not a destination.” Those of us dealing with information security have a similar saying, “Security is a process, not a point project (or product.)” It’s a great saying and I’m willing to bet it’s probably one of the few statements related to security that you could get a near majority of security professionals to agree upon. The problem is that while we may all agree that this is a true statement, most information security programs are not built and managed in a way that reflects this belief.
To illustrate my point, these are some of the common symptoms that point to a lack of focus on security as a process that I have seen in nearly all of the assessments I have conducted throughout my career:
Staff is overburdened with basic day-to-day operations or maintenance of existing security controls and has limited or no time to focus on designing or implementing needed improvements
Belief that “As soon as we get Product X up and running, all of our security problems will be solved.”
Security processes are not documented and often performed in an ad hoc manner
Excessive “shelfware” – numerous security products purchased but not deployed or utilized to their full capabilities
New security tools are purchased without proper consideration for staffing requirements
Business Units or other IT departments frequently complain that security is a roadblock
Security teams learn of new systems coming online after they are in production
Lack of focus on fundamental security practices like system hardening, patch management, and/or vulnerability management
Unclear or continually shifting priorities for the security program
While the symptoms are bad, the results of this lack of focus on security process are even worse. One only has to look at recent headlines related to recent attacks, or peruse the Data Loss Database (http://datalossdb.org) to see that in spite of the billions of dollars that have been spent on information security programs; we really aren’t slowing down the attackers. Too much emphasis on point solutions and failure to identify and address the real root-cause weaknesses in information security leave companies vulnerable to attack.
The Problem with Information Security Risk Management
Over the past few years we have seen the rise of various risk management methodologies like FAIR, OCTAVE, and those from NIST. While these frameworks and others like them are useful in mature organizations, they are often challenging to implement for smaller or less mature organizations to effectively implement. Even then, there is still reliance upon estimations of Annualized Loss Expectancy (ALE) or some variant thereof. Other risk management frameworks factor in “Management Judgment” as a means of weighting incident likelihood scoring.
If you have ever been in a meeting where scores based on management judgment or ALE have been used, you know the abyss that these conversations often fall into never to emerge with a useful plan. Worse yet, Manager ‘A’ who doesn’t have a clue about security but has tons of political clout can trump the best efforts of the security team to effectively and appropriately address risks.
The Successful Alternative: Process Thinking
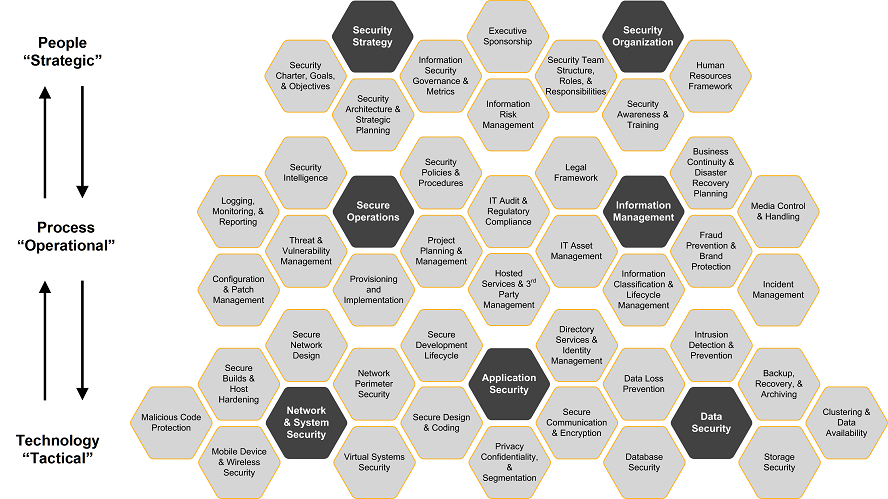
According to dictionary.com, a process is defined as a systematic series of actions directed to some end. I define the information security process to include everything that a company does to prevent or reduce the occurrence of data breaches, unauthorized disclosure of sensitive information, data loss, and/or loss of availability/denial of service. Broadly, this can be divided into seven (7) core process areas and forty-two (42) unique elements that must be addressed in order to provide a comprehensive approach to information security. This breakdown of process areas is illustrated in the Symantec Security Management Model:
Within each of these elements, there are numerous processes and/or technical controls that must be managed and maintained in order to achieve their intended results. These processes and controls are not isolated to a single element in the model, rather they are often interwoven across various elements and outputs or outcomes from processes in one element may provide inputs into other elements. All of these elements work in concert to provide a holistic framework for information security and, if properly implemented, should provide an organization with a solid security posture that is resilient to all but the most determined and sophisticated attackers. On the other hand, failure to properly implement and manage these processes will lead to the increased occurrence of information security incidents.